Data privacy and security is rarely out of the news at the moment. If it’s not the latest Facebook data scandal, it’s companies like Marriott and British Airways falling foul of the GDPR and facing severe financial penalties.
The majority of countries and territories have put legislation in place with the aim of protecting personal data and holding companies accountable for its safekeeping.
Central to this legislation is the concept of Data Sovereignty.
What is Data Sovereignty?
Data Sovereignty refers to the concept that data should be subject to the laws of the nation or territory where it is collected.
By crystallising this principle into law, governments have aimed to better protect their residents’ data and have also presented a new range of challenges to businesses obliged to store and use that data.
In particular, the increased prevalence of cloud computing has meant a greater focus on where data is stored and processed.
Companies such as Gatekeeper, which uses the cloud to store its customers’ contract and vendor data, are obliged to make sure that customers’ specific data sovereignty requirements can be met.
Data Sovereignty and the Cloud
Cloud computing has had a transformative effect on businesses’ ability to scale and to store vast amounts of data at comparatively low cost.
It’s at the heart of near-enough every large technology business today.
While the benefits of the cloud to the end-user are being able to access software and data from anywhere with an internet connection, the hardware behind the cloud takes the form of physical data-centres, often in remote locations.
It’s the location of these data-centres that is crucial when it comes to meeting data sovereignty requirements, whilst working with cloud solutions.
Companies that have only one global “instance” of their cloud solution may struggle to meet the data sovereignty requirements of potential international customers.
In turn, those potential customers need to fully understand the legislation that they’re working under and then look to find a suitable, compliant solution with which to trust their data.
Data Sovereignty and Contract Management
Contracts contain a wealth of personal and confidential information, which place them right in the firing line for data privacy legislation.
Managing contracts in a way that’s in line with that legislation is a key responsibility for internal legal teams and any other parties responsible.
Assuming a business uses, or intends to use a cloud-based contract management system, these are some of the key areas for consideration:
- Where, geographically, does the CMS intend to host your contract data? Some companies, like Gatekeeper, offer you a choice of global locations to make sure that your data can be stored in an appropriate and legally-compliant location. Others simply offer one location and that may not be compatible with your specific legislation.
The consequences for breaching this legislation can be extremely significant as well, as we’ve seen with both Marriott and BA earlier. - Within the Contract Management System may be particular services or functions that require your contract data to be ported. If the system uses third parties for functions like OCR search, online document editing or electronic signature then this could result in your data being transferred between locations.
It’s important to question whether this is the case and understand whether this is compliant with your local data legislation and internal policies. - Consider their engineering team’s procedures and how that might impact on the location of your data. For example, if they’re developing new functionality relating to your version or indeed more generally, ask whether that could lead to your data being replicated into another global location.
- Disaster Recovery Plans are a vital component of any business’s operations. Consider how your prospective CLM partner intends to back your data up, whilst still respecting data sovereignty requirements.
Will any back-ups still be within your chosen jurisdiction? - Do they have any external certification for their claimed data security credentials? Look out specifically for ISO 27001 certifications, which is considered among the gold standards for information security management.
- In addition to looking for evidence of external certifications, it’s worth reviewing all their security documentation to ascertain whether information security is something that is taken seriously by your prospective partner.
You can take a view on how closely it’s tied into their operations by looking at the information they’re prepared to share and publish on the subject.
Summary
Data sovereignty is a key pillar of data security and one that has to be addressed when it comes to contract management.
The information contained within your business’s contracts must be kept confidential and stored according to relevant local and international legislation.
Gatekeeper offers a choice of global locations to make sure that your data can be kept in compliant fashion. You can choose from five global instances:
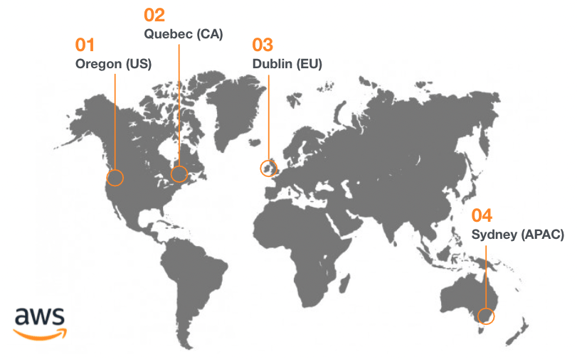 Gatekeeper's four global instances, covering the US, APAC and Europe
Gatekeeper's four global instances, covering the US, APAC and Europe
Not only that, Gatekeeper is ISO 27001 certified and regularly commissions independent penetration testing to make sure that our systems remain entirely secure for our customers.
To find out more about how Gatekeeper can support your information security requirements, and work within your business’s data sovereignty constraints, please contact us today.

.png)
.png)
.png)
-4.png)