As your business grows, it may become more inclined to outsource different functions of its processes to streamline in-house efforts, run more effectively and even increase profitability. However, introducing third-party vendors to your business also introduces different types and amounts of risks.
To avoid business and contract risk, effective vendor management and due diligence are required. A Service Organisation Controls Report – or SOC Report for short – should form part of your best practices when assessing and monitoring your vendors.
Below, we take a look at what a SOC report is, the differences between the three categories of report available and the differences between SOC reports and ISO certifications.
What is a SOC report?
A SOC report is an attestation by an independent auditor or Certified Public Accountant (CPA) firm that provides an overview of the compliance controls put in place by your vendors in regard to your outsourced functions.
Why should you request a SOC report?
By requesting a SOC Report from your vendor, you will be able to understand how they’re running, what controls are in place and how their processes impact your business on an operational and risk level.
If your vendors have the right controls in place, SOC Reports will give you assurances that everything you’re outsourcing is compliant with regulatory requirements.
In the opposite scenario of poor performance, SOC Reports give you the opportunity to identify any operational gaps or any weaknesses in the controls your vendors currently have in place.
Examples of potential gaps could include data being lost or unauthorised payments being processed under your vendor’s responsibility. You can work with your vendors to improve these aspects to ensure that risk across your business is mitigated.
Understanding SOC Reports
If your business is regulated and looking to outsource high-risk functions, vendor assessment and SOC Reports become crucial. The type of SOC report you request will be based on different criteria.
In both instances, the reports outline whether or not your vendors have the right practices in place to help you comply with regulations.
SOC 1
This report relates to the internal controls that your vendor has put in place for financials and accounting. It helps your business to understand how well a third-party vendor looks after its books.
SOC 1 will give you an idea of the accuracy and completeness of their financial reporting. SOC 1 reports will always be considered as confidential information by vendors, so not for publication once received."
There are two different types of SOC 1 reports, so it’s important that you ask for the right report.
SOC 1 Type I outlines the controls your vendor has in place during a single point of time. The benefits of this report are fairly limited as they only provide a snapshot of what’s going on. Risk can easily increase after this snapshot is provided, without your business even being aware of it.
SOC 1 Type II is the more insightful report as it provides an audit over an extended period of time, usually up to 12 months. These reports are more reliable as they are able to effectively demonstrate the robustness of controls in place. Type II reports gives businesses a more accurate overview of how risks are being minimised and should be the chosen report if available.
SOC 2
There are fundamental differences between SOC 1 and SOC 2. SOC 2, thus, should not be considered as an upgrade to SOC 1. While SOC 1 pertains to financial reporting, SOC 2 examines your vendors’ controls over the following Trust Services Criteria (TSC):
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Your business should ask for a SOC 2 report from its IT vendors in particular.
This independent audit can provide metrics on how your vendors are providing secure and available solutions to support the outsourced functions of your business.
Similarly to SOC 1, SOC 2 also has two variations, both considered as confidential information by vendors, so not for publication.
SOC 2 Type I simply confirms that controls are in place, whereas Type II confirms that as well as controls being in place, they are working. To get the best view of how well your vendor is performing when it comes to protecting your data and providing secure solutions, a SOC 2 Type II report is the best version to request.
SOC 3
Don’t make the mistake of assuming SOC 3 is the ultimate report. In fact, it’s quite the opposite. It’s less comprehensive than its counterparts because of its public availability.
A SOC 3 report won’t include the same level of information that can be obtained from a SOC 2 Type II report."
As a result, it’s simply a summary that is best used as part of your due diligence when researching potential vendors.
Is a SOC 2 report the same as an ISO certification?
When it comes to choosing a risk management framework, especially when outsourcing your IT contracts, you might be torn between choosing a vendor that uses the SOC 2 framework, a vendor that commits to following the guidelines provided by ISO 27001 or indeed have your choice restricted by applicable regulations.
The good news is that, on the whole, these two methodologies cover similar processes and technologies that protect sensitive data.
The most significant difference is that ISO 27001 largely focuses on the development and maintenance of an information security management system, whereas SOC 2 focuses on whether or not the controls to protect sensitive data have actually been implemented, and how well."
In summary, this means that while ISO 27001 and SOC 2 both review design effectiveness, SOC 2 also covers operating effectiveness. ISO 27001’s target is compliance with the standard at a point in time; SOC 2’s target is assurance that controls are being followed in practice at a point in time or a period of time.
Of the five SOC 2 Trust Services Criteria outlined only the first is mandatory, making this framework far more flexible for your business’s needs.
A vendor that uses ISO 27001 to control data security has a far more rigid framework than SOC 2 requires. To achieve compliance with ISO 27001, your vendor must:
- Conduct a risk assessment
- Identify and implement security controls
- Review each control’s effectiveness on a regular basis
The remaining difference between ISO 27001 and SOC 2 is the certification process. When it comes to certification, vendors using the ISO framework must be audited by a recognised ISO 27001-accredited certification body. As mentioned earlier, a SOC 2 attestation report can be completed by a licensed CPA.
How Gatekeeper helps you to manage SOC requirements
Gatekeeper’s core platform provides workflow and compliance automation, helping you to better manage your SOC requests and requirements.
Receive automated alerts for report renewals
Gatekeeper makes it easy to stay ahead of compliance by helping you to get organised. You can set and receive automated reminders when key dates are on the horizon – particularly useful if the validity of a SOC report is about to expire or if you need to receive a report by a specific date.
These automated reminders will help you to act ahead of time, so you can ensure your business is always up-to-date with regulatory requirements. You can have confidence that you won’t miss any renewals and left facing business risk.
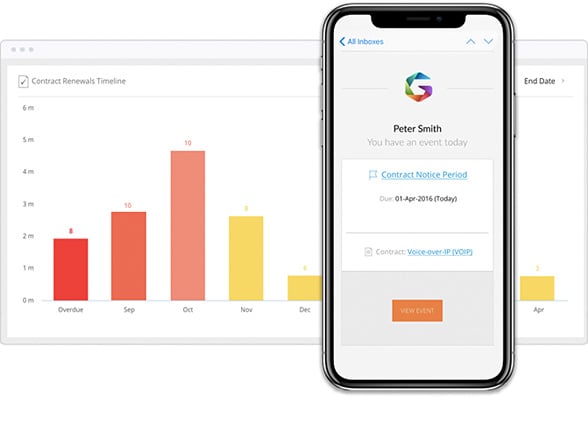 Renewal notifications from Gatekeeper
Renewal notifications from Gatekeeper
Easily and securely store SOC reports
Once you have requested and received a SOC report from your vendor, you can store them in a centralised repository. With Gatekeeper, you can attach a SOC report specifically to the vendor, storing all the information you need in a single, easily accessible, cloud-based location.
You can also set permission levels for different users across your organisation, ensuring that only relevant parties can access the SOC report. This keeps compliance documents secure, preventing potential loss or the report being moved to a different part of the repository.
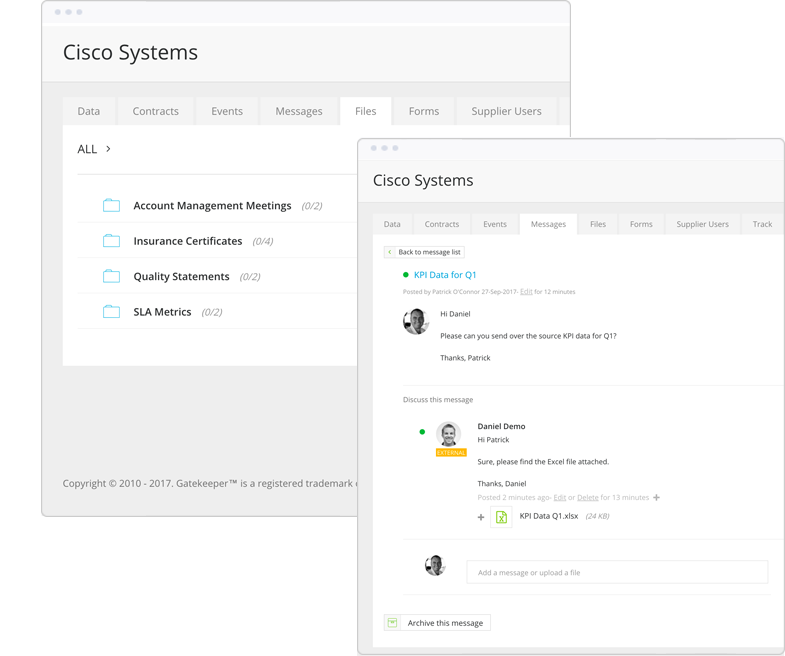 Store reports against the master contract with Gatekeeper
Store reports against the master contract with Gatekeeper
View a full audit trail of activity related to SOC reports
If your business is highly regulated, it’s crucial to keep your auditors happy. Gatekeeper supports in every area of compliance, allowing you to track when the SOC report was carried out, who was responsible for it externally and who has managed the report internally. With complete audit trails that are fully defensive and searchable, it’s never been easier to be compliant.
Summary
The risks of ignoring SOC reporting or ISO compliance can be detrimental to your business. When it comes to finance, data security and overall operations, you need to be able to outsource with confidence. Introducing vendors to your business inherently adds risk and SOC reports are one way of mitigating potential gaps.
SOC reporting can strengthen relationships between your business and its vendors, which improves the overall service provided to your customers.
These reports allow trust and transparency to be at the centre of your approach to regulatory compliance, as well as provide valuable insights into your vendor management, control governance and state of security.
If you want to find out more about effective vendor management and minimising overall risk, please contact us today.

.png)
.png)
.png)
-4.png)