Managing contracts is an ongoing task with many moving parts, especially for businesses that have complex portfolios, engage suppliers that are geographically dispersed or if the business is scaling at pace.
As contracts, supplier requirements and regulatory requirements never stand still, there are a number of factors that can disrupt and fragment effective contract management.
These include:
- The number of contracts needing regular management. These are the ones designated as critical or important, typically a very small subset of the overall number of active contracts, and that might be a large number nonetheless
- The almost constant need to reschedule some pre-planned deadline-driven activities due to the arrival of new requests and issues as outlined below.
- The random arrival rate of:
- new contracts to be reviewed, negotiated and implemented
- requests for amendments to contracts
- unexpected contract events, issues or situations and other firefighting activities that demand a quick response
- requests for specific information about specific contracts or groups of contracts from internal people, auditors or regulators
Whether a key contract needs immediate attention, a compliance certificate is reaching expiry or an issue needs escalating to stakeholders, those responsible for contract management need to be able to quickly identify issues, find critical information such as key clauses or dates and communicate effectively with the relevant suppliers and stakeholders.
If your business has a fragmented approach to contract management in terms of storage, processes and communication, it will fail to create a single source of truth.
Only when contracts are centralised and processes are aligned can your business have confidence in the accuracy of its portfolio, the stage each contract is at and its ability to respond proactively to potential risks.
Visibility and searchability are two aspects of successful contracting standards that will serve your business best here. Building a single, accurate view of your portfolio and the information it contains relies on using best practices for managing your contracts and the data they contain.
In this article, we’re going to look at five key contract management strategies for creating your single source of contract truth:
- Creating a contract documents repository
- Categorising your contracts to make them easier to find
- Standardising contract document naming conventions
- Accurately capturing contract data
- Setting appropriate permissions for accessing contract information
Strategy 1: Create a Contract Documents Repository
Conventional wisdom has it that all contracts and related documents in an organisation should be housed in contract repository software.
This makes sense because having unfettered access to the information contained in those documents enables the organisation to understand what’s being done where, the attendant costs, obligations and risks incurred, and the value delivered across the board.
This strategy is about looking at the big picture. In respect of the total contract inventory, it’s not just a matter of collecting contract documents, which can be a difficult problem in its own right. It requires a holistic look at what is needed to fulfil the purpose of extracting value from the information locked-up in those documents."
After all, there could be any number of what-ifs to consider that can complicate things operationally, such as:
- What if the organisation has to-date applied a laissez-faire, standards-free approach to establishing contracts where everybody has made up their own rules, for matters like document naming, contract status settings and the values used for other attributes common to most contracts? Who does or pays for the remedial work needed to establish a coherent and consistent set of contract data standards for the entire organisation? How can broad adoption be achieved?
- What if the organisation uses a wide range of currencies in its contracts? Is there a need to establish a single ‘reporting’ currency to allow consistent point-in-time exchange-rate calculation of the value of active contracts individually and in total?
- What if no signed copies of operational contracts can be located, or multiple signed copies exist but are undated, in the records of both the organisation and the involved third parties? Would it be feasible to agree with the third parties to terminate such contracts and negotiate new contracts from scratch where the requirement still exists? What’s the likelihood of any third party preferring to play hardball in this respect? How feasible is it to resort to the courts?
- What if it turns out that there are more paper contract documents out there than electronic versions, or scanned versions that are all but illegible? Who will be responsible for creating, or obtaining and paying for, high quality electronic versions of the required documents?
- What if the organisation has subsidiaries located in different countries, where contracts are written in the native language of those countries and not that of the organisation’s headquarters? Is there a need to have such contracts translated into the HQ language, to allow for searching across the entire inventory? If so, should this be done as a one-time event on receipt of the native-language version, so both copies can be loaded into the repository, or should all contracts executed by the subsidiaries be side-by-side native and HQ language versions? Are the skills available internally to accurately translate legal concepts from different legal systems into something recognisable in the HQ language? Which language version takes priority as far as HQ is concerned? Who pays for the translation work?
- What if the organisation’s subsidiaries actively or passively resist timely collection and provision of current versions of all their contracts, or participation in the development and implementation of a consensus approach to dealing with various what-ifs? Will senior organisational management willingly step in to help resolve such situations if lower-level appeals to senior subsidiary management have no effect?
Hypothesising about potential what-ifs can be useful if ideas for value extraction from the contract documents are well-formed. But it’s well-known that fact can be stranger than fiction, so looking inwards should be accompanied by looking outwards to the subsidiaries, so a realistic list of what-ifs can be assembled.
This means unearthing the type of situations, the what-ifs, that can interfere with value extraction, then developing, socialising and agreeing on options for dealing with the occurrence of a what-if with the organisation’s subsidiaries.
Complete success at getting this right might not always be achieved on the first go or even the second. The complexity of what-ifs and their solutions can affect this, as might the level of available skills, and the experience and attitudes of all the people involved.
Finally, the centralised or decentralised operating model adopted by the organisation, as well as an inevitable amount of organisational inertia, can play a big part.
Strategy 2: Categorise Your Contracts To Make Them Easier To Find
Once you have addressed the potential what-ifs throughout your organisation and created a standardised and centralised way to store your contracts and metadata, you will need to organise them.
Simply storing contracts in a single location, without any order, won’t necessarily help your teams. It just moves potentially inaccurate and duplicated information into the same place.
Placing objects into classes or groups – categorisation – can make it easier to find those objects. It also allows specific things to be done or not done by, for, to or with members of specific groups.
This strategy is about capitalising on collections: allowing attention to be selectively focussed on what the organisation considers important to know about specific aspects or characteristics of the supplier-contract ecosystem, many of which might not be readily discernible from the contract documentation but have to be derived using rules."
The basis for categorisation might be an innate characteristic of the object, say its colour or weight, or a label with derived values assigned according to a clearly specified set of rules, such as condition (new or used, based on inspection), usage level (low, medium or high, based on the number of times used, with thresholds used to indicate levels) or RAG Status (red, amber or green colours associated with a subjective label such as the level of risk).
-1.png?width=1300&name=RAG%20(1)-1.png) See the RAG Status of your contracts within the Gatekeeper Dashboard
See the RAG Status of your contracts within the Gatekeeper Dashboard
For CLM purposes, a wide range of categorisations might be desirable to adequately describe attributes of contracts, suppliers and other objects of interest.
Organisations using a CLM system could find that the system allows for all the categorisations needed plus some that might be not so useful.
On the other hand, insufficient categorisations may not be available either in the system’s core offering or in any customisation capability. That could well be an important factor in selection of an appropriate CLM system.
Of course, for a manual CLM operation, say using spreadsheets, there is plenty of scope for creating as many categorisations as required. Some useful categorisations, sample settings and their sources might include the following.
Contracts
Contract type: Lease, MSA, NDA; from contract
Export rules apply: No, Yes; assigned
Important contract: No, Yes; assigned
Owning business unit: Finance, HR, IT; assigned
Category: Computer Equipment, Consulting, Software, Telecoms; from contract
Personal data handled: No, Yes; from contract
Risk potential: Low, Medium, High; assigned
Sole supplier for category: No, Yes; assigned
SuppliersBusiness continuity plan grade: Low, Medium, High; assigned
Important supplier: No, Yes; assigned
Location of supplier’s main production facility: country name; assigned
Modern slavery risk: No, Yes, Unknown; assigned
Risk potential: Low, Medium, High; assigned
Status: Active, Inactive, Do not use; assigned
Supplier type: Commodity, Operational, Strategic, Tactical; assigned
Supply chain visibility: Low, Medium, High; assigned
Date-driven contract-related events
Critical event: No, Yes; assigned
Due date modifiable: No, Yes; assigned
Responsibility: Joint, Them, Us; assigned
Major event: No, Yes; assigned
Status: Done, Done but late, In progress, In progress but overdue, Pending, Pending but delayed; assigned
Categorisation provides the next level of depth and flexibility for your repository, enabling finer control over contracts as well as some clear options for reporting.
Strategy 3: Standardise Contract Document Naming Conventions
Categorising your contracts is just one of many steps you’ll need to implement when creating a single source of truth.
The ability to search and find information quickly is just as important as building the repository itself. Standardising document naming conventions helps your teams to work consistently and makes information easy to locate.
This strategy is about convenience: helping people to save their precious time by not making them work to find information that can be readily provided to them up front, or by making them apply local workarounds so documents can be easily found.
A document name should be more than a simple label, it should provide compact information on what a document is about.
Here’s why. A typical electronic filing system consists of directories with multiple levels of subdirectories. The directory path to a specific document might look like the following:
Contracts > BigCorp > Services > Telco > UK > Data Services Agreement 2020.pdf
Visually, it’s pretty clear what the document is about, because the path names provide context. That is unlikely to be the case when the document is in motion and the context is left behind.
Say the document is attached to an email that says ’Here’s the document we talked about last week’ and the email sent. The recipient may or may not clearly recall the discussion or the document and really has no option other than to open it to find out.
If the recipient then wants to save the file, a meaningful directory structure like the one above might be needed to allow easy future selection of that local copy of the document.
Alternatively, the recipient could rename the document to include enough information, like supplier name and country, to find it wherever it is saved. The document name could end up as something like ‘BigCorp UK Data Svcs 2020.pdf‘, for example.
However, if the document was originally named as above or similar to be self-identifying regardless of the clues provided by the directory structure, then everybody benefits.
Within the bounds of sensibility, readability and practicality, almost anything that really assists with document self-identification could be used.
Standards for abbreviations of common words will likely be needed, recognisable but short names for suppliers should be agreed, formats for dates that allow sorting of document names by date order should be used, and so on. Creativity without obscurity is the aim.
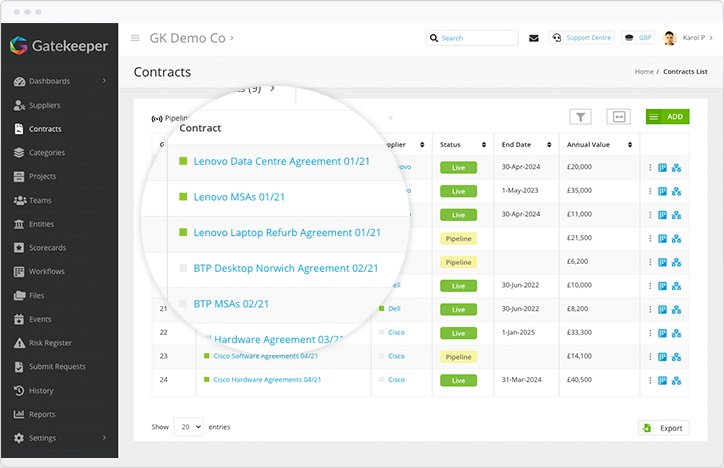 Good naming conventions make contracts easy to find in Gatekeeper
Good naming conventions make contracts easy to find in Gatekeeper
There is no point in trying to cram too much information into a document name, just because it might be useful to some people some of the time.
Just enough is needed to be reasonably assured that the right document can be selected based on its name. Other details can then be accessed as required by opening the selected document. Compliance with the naming convention should be strongly encouraged.
Strategy 4: Accurately capture contract data
When the contracts have been categorised and named under a standardised convention, time and attention needs to be given to what data will be extracted and how. Accuracy is crucial here.
By having confidence in the available data, stakeholders can make informed business decisions, such as whether to renew a contract, with confidence.
A lot of information might need to be recorded about contracts to facilitate their ongoing management and increase their discoverability from many different angles. This information can be sourced in different ways, such as:
- Extraction from the contract itself: start date, term, governing law
- Derivation as a characteristic or status indicator: active / inactive, currency used
- Assignment of a label of some sort: importance, risk rating.
Development and adoption of standards covering the formatting and content of such information, particularly when supported by technology, leads to improved data consistency and quality which in turn enables more accurate search results.
This strategy deals with consistency and trust. When applied to shorthand data, it makes meaning transportable and universal, helps to minimise confusion, and allows quick recognition and treatment when new data values and meanings are required due to changing circumstances. It should also increase the level of trust in the completeness of the results of certain types of search."
Various techniques can be used in data standards to help achieve consistency and brevity:
1. Abbreviation
Official or common usage abbreviations can be used when applicable, such as:
- Countries: New Zealand > NZ (ISO 2-letter country code)
- States within countries: British Columbia > BC
- Street types: Road > Rd
- Directions: North > N.
Abbreviations in common use or high familiarity in the organisation or its industry could also be used where practical.
2. Coding systems
Using shorthand codes to replace often verbose descriptive text is a fairly common-sense practice. For instance, a ranking of some sort could be based on a numeric scale with values between 1 and say 5, where 1 is highest, or using representative characters to express the intended meaning, like ‘H’, ‘M’ and ‘L’ for high, medium and low.
A coding scheme can be quite complex if multiple characteristics need to be included in a single code. For instance, a product code might have designators for type, colour, material and so on, based on a position in the code and a number of characters to express these types of variables.
Whatever type of coding scheme is used, its use within the organisation must be mandatory in order to deliver consistency of meaning. Automation can play a big part in ensuring that only valid codes are used.
3. Precision
For any number of reasons, some types of information may need to be expressed in a very precise manner.
Consider uniqueness as a reason. A supplier to an organisation might commonly be referred to as, say, ‘IBM’.
To IT, this would probably be construed as a reference to the technology giant International Business Machines Corporation. To HR, it could mean the overseas placement support firm I’ve Been Moved. To Finance, it might be understood as consultants Iverson, Bowen and McKenzie.
The precision required here to prevent duplication and confusion is achieved by the use of the supplier’s full legal name to provide the necessary uniqueness. Such use should form the basis for a standard to be applied to supplier name, not the commonly used abbreviation."
Another form of precision standard might be applied to the naming of clauses used by the organisation in its own contracts.
Relating the clause name to the subject matter of the clause, like Payment Terms or Governing Law, and making its use consistent wherever such a clause is used, facilitates an electronic search of contract documents for the existence of a specific clause type.
If a clause name is fairly representative, perhaps supplier-provided contract documents will also be found by the search if they also follow a similar standard.
Naming clause types in contracts alleviates the invisibility problem often associated with sub-clauses that are wrapped up in a Miscellaneous clause. In such cases, extra discovery work about a Miscellaneous clause’s contents is likely warranted.
Creating data standards would ideally get done very early on in the CLM journey, but certainly before any implementation of an automated CLM system. "
The nature of the information required to record contract, supplier and other related details needs to be identified.
Next, any information where use of a coding system can make life simpler should be determined, and the various options for each coding system proposed, socialised and set.
Documentation should be produced, with rules and guidelines built-in to any automated CLM system to the extent practical.
Strategy 5: Set Appropriate permissions to control access to data
Contracts and their metadata should not be available to any and all individuals throughout your business. When keeping contracts in a centralised location, restricting access and the ability to edit, delete or share data is paramount - especially if regional laws such as GDPR are in place.
The strategy here is containment and tracking: limiting access to all confidential information on a need-to-know basis, logging every access and change made to confidential data, and periodically checking that all access rights are current."
Many aspects of a contractual relationship between two or more parties, such as pricing, intellectual property or even the existence of the relationship itself, can be considered as confidential by one or more of those parties, whether stated so explicitly or not.
Since unauthorised disclosure of confidential information by the organisation can result in a range of undesirable or unrecoverable consequences for the owner of that information, the disclosing organisation and the individuals involved, adequate steps need to be taken to minimise the opportunities for such disclosure.
At the same time, there is a need to protect much other contract-related data from being altered or deleted without authorisation.
A straightforward approach to managing confidential information might include:
- Documenting exactly what contract data items are, or could reasonably be considered to be, confidential. Doing this upfront for every new contract leaves no room for doubt, and can be useful if a terminating contract contains obligations covering the return or destruction of confidential information
- Identifying who needs what type of access to which specific confidential data items, then assigning appropriate access rights to those items to individuals and / or roles
- Educating the people granted access to confidential information about the importance of compliance with confidentiality obligations and the possible consequences of non-compliance
- Maintaining a date-stamped audit trail of accesses to confidential data and changes made to it
- Managing the currency of confidentiality classifications and access rights through stringent change control. This implies a timely and foolproof method for receiving advice from the appropriate organisational authority about changes needed to such classifications and rights as people move into, around and out of the organisation.
Wrap-up
Creating a single source of truth by building a repository, standardising data capture, appropriately categorising your contracts and assigning the right levels of access to individuals gives your business far more control over its portfolio and more confidence in the data it contains.
By having a single pane view of your entire portfolio, you will be able to identify and resolve bottlenecks, spot upcoming risks and mitigate them ahead of time and improve communication across the business and its stakeholder by having accurate data to hand.
The above contract management strategies are best implemented alongside a dedicated contract management solution to help you search your portfolio and find information more efficiently.
If you’re ready to implement some of the strategies above, or want to know how Gatekeeper can support your existing approach to contract management, get in touch today.
















.png)
.png)
.png)
-4.png)